Fixing the Remote Access Service IP Configuration Error | Step-by-Step Guide
By webavior 19-09-2025 71
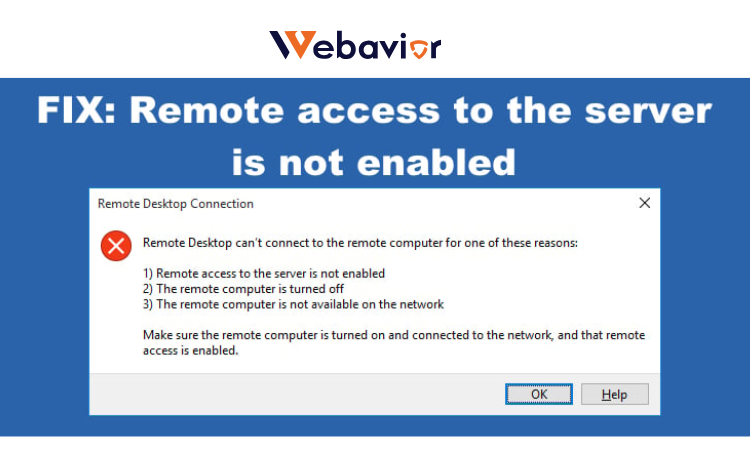
You think this: you have been an hour into setting up a VPN with your distributed team on a windows server, everything has been fine until the Remote Access Service displays the terrible “IP configuration is unusable" error. Connections break, patients complain and your productivity stalls. That is not a small glitch, it is Event ID 20225 in the RRAS logs that the server is not able to issue out valid IP addresses out of its pool or through DHCP, essentially disabling remote access. This mistake stings particularly IT pros operating in hybrid environments, where every site to site tunnel and dial-up relic are being driven by Routing and Remote Access Service (RRAS) in Windows Server 2016 through 2022 environments. It is frequently due to minor misconfigurations such as depleted IP space or routing glitches that propagate to outages.
At the end, you will not only eliminate the current problem but also are able to see patterns to avoid recurrences. Ensure you are in the role of an administrator, have RRAS installed, and a fast VM snapshot as a backup before proceeding with this step, on the assumption that you are comfortable with the basic server administration but require specifics of RAS firepower.
Prerequisites and Initial Diagnostics
Be prepared with good diagnostics to prevent guesswork before you make any changes to configs. The first thing you need to do is to make sure that you are in the right environment, open up PowerShell and run Get-WindowsFeature RSAT-RRAS to ensure that the Remote Access role is installed and active. In case it is not there, Add it with Install-WindowsFeature RemoteAccess -IncludeManagementTools. The second step is to verify the patch level of your server - old KBs may be known to cause IP problems, so go in search of updates through Windows Update or Get-HotFix.
Logs are your first ally here. Launch Event Viewer and navigate to Applications and Services Logs > Microsoft > Windows > RemoteAccess. Filter for errors around ID 20225 or 20271; these often detail the exact failure, like "no available addresses" or relay timeouts. Export the logs to a CSV for easy parsing—something like Get-WinEvent -FilterHashtable @{LogName='Microsoft-Windows-RemoteAccess/Operational'; ID=20225} | Export-Csv -Path C:\RAS_Errors.csv in PowerShell will do the trick. This gives you timestamps and context tied to recent changes.
To check the health pulse of your system in a fast way, press to the command line and use ipconfig /all which will scan your interfaces in your server to identify any IP conflicts or odd subnet. Then netsh ras show clients must show running sessions, and again: when it is empty although there is expected traffic, then it is blocking assignments. Get-RemoteAccess cmdlet is a leaker of IP pool status (start/end ranges and utilization) available in more detail in PowerShell: Elevate to PowerShell and get more information. Beware of such red flags as zero addresses available or subnets mismatched. When you have traffic issues, fire spin Wireshark on the server NIC to capture DHCP packets or IKE packets, you want to filter UDP port 67-68 packets.
Pro tip: always snapshot your VM pre-changes; routing tweaks can cascade into broader network woes if they go sideways. With these baselines, you're primed to isolate the culprit without blind stabs.
Step 1: Verify and Reset IP Address Pool Configuration
The majority of IP unusable errors are caused either by the inexhaustible nature of the static address pool in RRAS, or a misranging between RRAS and your LAN. Imagine that it is the IP vending machine of a server that is jamming--no coins (requests) are expensed due to empty slots or blocked slots. To remedy this we will check and recalibrate the pool beginning with the GUI just to see but will use PowerShell to be precise and write scripts.
Access the Routing and Remote Access console through typing in rrasmgmt.msc in Run. Right-Click on your server node on the left window and click Properties and then change to the IPv4 tab. In this case, make sure that the “static address pools option is activated- this is more stable than DHCP in small configurations. Click pool button to edit: check your range: say 192.168.1.100 192.168.1.150 do not include in your current scopes of DHCP or local subnets. Should it do so, push it to an empty block such as 10.0.0.100-10.0.0.200, make the changes and restart the RemoteAccess service with Restart-Service RemoteAccess using a higher prompt. This resets any stagnant leases and reconfigures.
For the command-line crowd, PowerShell shines: first, peek at the current setup with Get-RemoteAccessServer | Select-Object IPv4AddressPool, which dumps the range and usage stats. If it's off, redefine it cleanly: Set-RemoteAccessServer -IPv4AddressPoolStart 10.0.0.100 -IPv4AddressPoolEnd 10.0.0.200. This is atomic and scriptable, perfect for automating across farms. A frequent gotcha is scope overlap—cross-reference with Get-DhcpServerv4Scope on your DHCP server to ensure no turf wars.
Check the step with verification: netsh ras show ipaddresses must list your pool with generating numbers of free slots. When it populates correctly it is likely that you are now nailing the nail on the head, otherwise add the next steps as quickly as possible.
Step 2: Troubleshoot DHCP Integration and Relay Issues
When your RAS is using DHCP to allocate dynamic IPs as opposed to using static pools, even a full reservoir can go to waste when the relay fails, and lease requests will be lost along the way. This is typical with segmented networks where the RRAS server does not happen to be DHCP host, the timeouts are silent and are mistaken as pool exhaustion.
Begin by auditing your DHCP setup: confirm the role is active with Get-DhcpServerv4Scope, ensuring scopes are authorized and have ample addresses. In the RRAS console under IPv4 Properties, if "From a specified range of addresses" isn't checked, toggle to DHCP mode—but only if your relay is solid. For relay configs, right-click IPv4 in the console tree, select New Interface, pick your internal adapter, and in the properties, enable the DHCP relay agent under Inbound Filters. Point it to your DHCP server's IP, like 192.168.1.10, then save.
Command-line relay setup is snappier: use netsh routing ip relay set interface "Local Area Connection" dhcp server 192.168.1.10 to bind it to the right interface. In PowerShell, amp it up with Add-RemoteAccessDhcp -InterfaceAlias "Ethernet" -RelayServer 192.168.1.10, followed by a service restart. Firewalls love to sabotage this—UDP 67/68 must flow freely, so punch holes if needed: netsh advfirewall firewall add rule name="DHCP Relay" dir=in action=allow protocol=UDP localport=67-68.
Test the relay by firing a simulated request; grab dhcptest.exe from the Windows SDK and run it from a client subnet, or tail Event Viewer for lease events post-restart. If grants flow, your dynamic assignments are revived—watch for intermittent flakes pointing to MTU mismatches on VLANs.
Step 3: Resolve Routing and NAT Conflicts
Routing table gremlins or NAT overloads often render IPs "unusable" by stranding them in limbo—packets route to nowhere, or translations exhaust mid-session. This flares up on multi-homed servers juggling internal and external traffic.
Kick off with a route dump: route print in cmd reveals the table; scrub for duplicates on your RAS subnet, like multiple paths to 10.0.0.0/24. In RRAS, under IPv4, add static routes if gaps exist—right-click Static Routes, new route to your remote network via the gateway. Persist it with route -p add 10.0.0.0 mask 255.255.255.0 192.168.1.1 metric 1. For NAT woes, navigate to NAT in the console, ensure your external interface is selected for masquerading, and if bindings are stale, delete and recreate: netsh routing ip nat delete interface "External" then netsh routing ip nat add interface "External".
PowerShell elevates this: Get-NetRoute | Where-Object {$_.DestinationPrefix -like "*RAS*"} filters suspects, and New-NetRoute -DestinationPrefix "10.0.0.0/24" -InterfaceAlias "Internal" -NextHop "192.168.1.1" injects fixes. On multi-NIC rigs, tweak metrics for priority: Set-NetIPInterface -InterfaceAlias "Internal" -InterfaceMetric 10 to favor the right path.
Verify with pings from the server to a pool IP, followed by tracert to trace clean hops. If latency spikes or drops occur, it's a sign to prune asymmetric routes—your RAS should now route like clockwork.
Step 4: Address Firewall, Security, and IPv6 Conflicts
Even with perfect pools, firewalls or protocol clashes can veto IP usability, blocking the handshake before assignment. Security layers add their own vetoes, from GPO lockdowns to AV overzealousness.
Audit Windows Firewall first: inbound rules for RRAS must greenlight GRE (IP Protocol 47) and IPsec ports (UDP 500/4500). Bulk-enable via netsh advfirewall firewall set rule group="Remote Access" new enable=Yes. For PPTP holdouts, add TCP 1723 explicitly. If IPv6 is lurking, it can dual-stack conflict—temporarily neuter it in RRAS Properties > IPv6 tab by unchecking forwarding, or PowerShell it with Disable-RemoteAccessRoutingDomain -AddressFamily IPv6.
Run a system file check too: sfc /scannow mends any corrupted RAS binaries, and scour Group Policy for RAS-denying restrictions under Computer Configuration > Administrative Templates > Network > Remote Access. Antivirus? Carve out exclusions for C:\Windows\System32\ras to dodge false positives.
Probe with Test-NetConnection -ComputerName localhost -Port 1723 or telnet equivalents; clean connects mean barriers are down. This step often uncovers the "invisible" blocks that diagnostics miss.
Step 5: Test, Verify, and Monitor Post-Fix
With tweaks in place, rigorize the fix through testing—don't trust a quiet console. From a client machine, dial up the VPN using the native Windows client; watch for seamless IP handoff in the connection status. Script it for repeatability: rasdial "MyVPN" username password /domain:domain.com logs the session, flagging any lingering errors.
Polling Server-side Poll Get-RemoteAccessConnectionStatistics to find healthy session counts without faults. Test with load: relevant: load assignments with several clients, or with the help of ostress.exe, and make sure that pools do not drop out of the load.
For longevity, bake in monitoring—a PowerShell scheduled task for daily checks: $pool = Get-RemoteAccessServer | Select IPv4AddressPool; if ($pool.Used -gt 80%) { Send-MailMessage -To admin@domain.com -Subject "RAS Pool Alert" -Body "Low IPs imminent!" }. If smoke persists, nuke and pave: netsh ras delete registeredserver clears the slate for a fresh RRAS install.
Tip You can use WebaviorVPN which offers the smart system to avoid these type of issues.
Conclusion
Addressing the Remote Access Service IP configuration is unusable error is reduced to layer upon layer; pool resets, DHCP relays, route cleanups, barrier audits, and incessant testing. You have now a set of tools to revitalize your VPN and make outages a side note.
Unless these measures are permanent, go to Microsoft Support with your logs they feed on Event ID 20225 deep dives. Post your victories or perversions in the comment box; which is the most outrageous RAS perversion that you have killed? To see more, see our IPv6 conflicts post or download the free RRAS checklist PDF.
Tags : remote access vpn